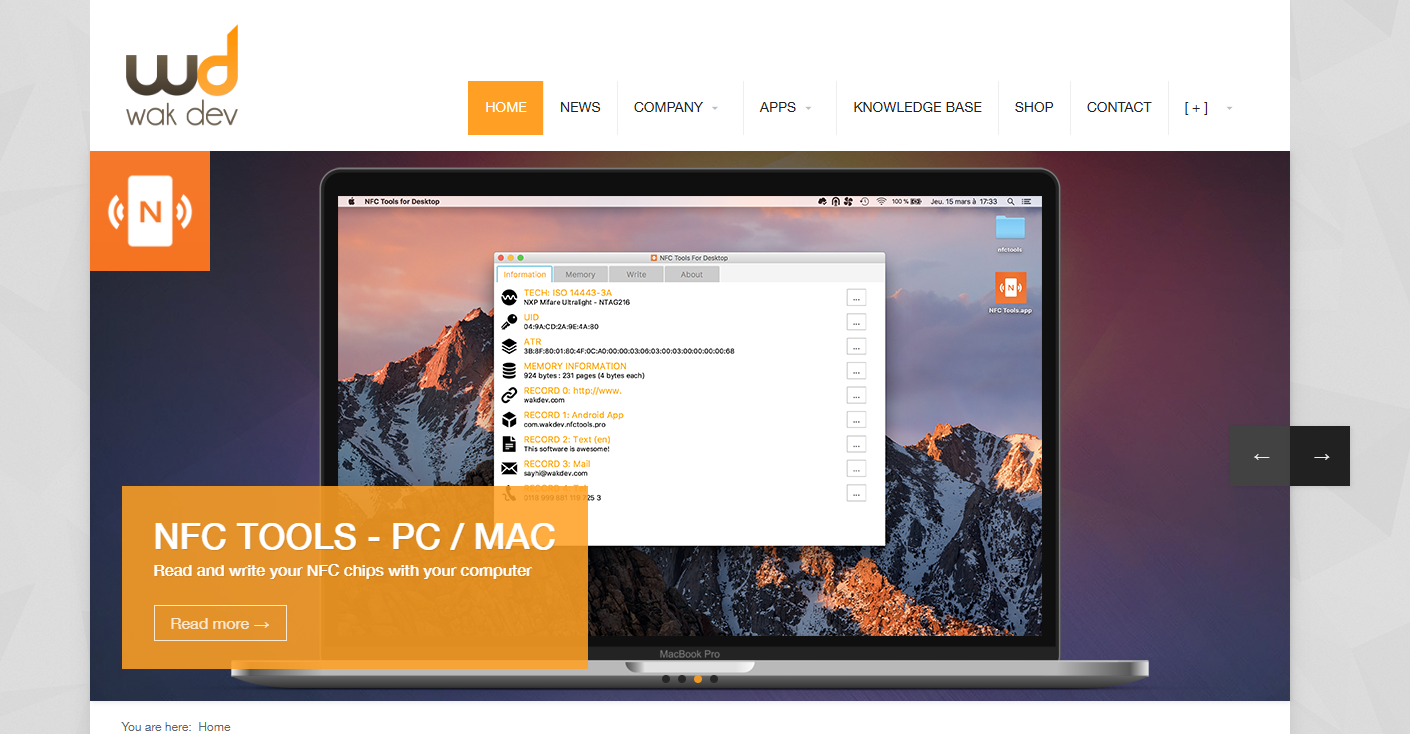
Today we’re going to offer you an article that’s a little different from our usual fare, since it’s less about going into the details of how to implement a SpringCard product than about presenting a small piece of software that can help you discover the world of NFC and contactless smart cards.
It’s called NFC Tools, and has been developed by Wakdev.