SCardSniffer is a new tool used to spy the exchanges between Windows applications and the smart cards or NFC tags that are accessed through a PC/SC reader (or coupler).
On a Windows computer, all card-aware applications communicate with smart cards or NFC tags through the system’s PC/SC library, winscard.dll.
winscard.dll then communicates with the PC/SC service, which in turns communicates with the reader’s driver, and then, at last, the reader communicates with the card or the tag.
By placing a software “hook” on top of winscard.dll, SCardSniffer makes it possible to see all the function-calls made by the application, including the APDUs exchanged with the card or the tag within SCardTransmit.
As most other softwares provided by SpringCard, SCardSniffer is totally free -provided you’re using it with a SpringCard device attached to your computer. Please refer to our portfolio of PC/SC products that are likely to be used with SCardSniffer.
WARNING
To be able to spy all applications that load winscard.dll, SCardSniffer installs a global DLL hook thanks to a so-called DLL Injection method that uses AppInit_DLLs registry entries (see https://en.wikipedia.org/wiki/DLL_injection for the technical background).
Some malware are known to use the same DLL Injection method, and therefore SCardSniffer is likely to be stopped by a suspicious anti-virus or anti-malware tool. If this is the case, please disable this tool while you’re using SCardSniffer (read DISCLAIMER below: you do this at your own risk). On some versions of Windows, AppInit_DLLs is disabled when secure boot is enabled. Please disable secure boot on the machine you intend to run SCardSniffer on (see https://support.microsoft.com/en-us/kb/2853424 for details).
DISCLAIMER
Downloading and verifying
SCardSniffer is available at https://www.springcard.com/en/download/find/file/sn16312.
This is not a self-installation package but a ZIP archive. The ZIP archive must be extracted into a folder which does not contains any spaces in its name. Recommended folder is C:\SCardSniffer
AppInit_DLLs registry entry does not support file names with a white space in them. If you try to execute SCardSniffer from a folder with a space in its name, the application with be unable to install its hook, and therefore unable to spy anything.
SCardSniffer is made of 4 files:
- scardsniffer64.dll is the hook for X64 systems,
- scardsniffer32.dll is the hook for X86 systems or for processes running in WoW64,
- SCardSniffer64.exe is the program for X64 systems,
- SCardSniffer32.exe is the program for X86 systems.
The .exe require Microsoft NET run-time v4.0.
The 4 files are digitally signed by SpringCard. Please verify that the files are genuine after downloading.
A 5th file (Newtonsoft.Json.dll) is used to save/load the log in a file (see http://www.newtonsoft.com/json for license).
Using SCardSniffer
You must have administrative priviledge to run SCardSniffer. If this is not the case, Windows will prompt you to run the software under the identity of a system administrator.
Launch the SCardSniffer executable that matches your system architecture (SCardSniffer32.exe or SCardSniffer64.exe), then launch the application you want to spy.
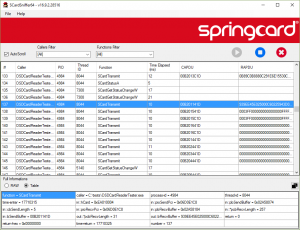
For every call to a SCard… function from winscard.dll, SCardSniffer shows
- The calling process (image name and process ID) and thread (thread ID),
- The name of the SCard… function (SCardEstablishContext, SCardReleaseContext, SCardGetStatusChange, SCardStatus, SCardConnect, SCardDisconnect, SCardTransmit, SCardControl and a few others…),
- The input parameters,
- The output parameters, and the return code,
- The time spent in the function, and the time between a function call and the next one.
When a line is selected, more details appear in the bottom panel.
SpringCard SCardSniffer is a handy tool to debug and profile the application you are developing!
The recorded lines could be exported to a log file (using JSON format), and reloaded for analysis at a later time. The log file may also be transmitted to SpringCard’s support to help diagnose what’s going on between your application and the reader (or the card through the reader).
The program has been tested on Windows 7, 8.1 and Windows 10, both X64 and X86. Due to the sensistivity of the DLL injection system (hook), it is not possible to assert that it will run OK everywhere.