5 years ago, SpringCard introduced SCardSniffer, a tool that spies the exchanges between Windows applications and the PC/SC subsystem. SCardSniffer works by introducing a hook over winscard.dll.
Although this method is still perfectly working in most cases, it comes with some technical complexity (1. the sniffer and the sniffed application must both run on the same subsystem, either Win32 or Win64, hence 2 versions of the sniffer and 2. the injection of the hook is likely to be disabled on security-enforced computers and 3. it may also triggers some antivirus/malware detection tools, which leads to an unnecessary stress).
SCardSniffer2 is a new tool that offers basically the same function, but with a much simpler architecture.
SCardSniffer2 installs a new virtual smart card reader and acts as a relay between this virtual reader and the real reader, where the real card is.
The application to be spied must be reconfigured to connect to the virtual reader (instead of the real reader); SCardSniffer2 is then able to record all the APDUs exhanged between the application and the card.
WARNINGS
1. SCardSniffer2 works by installing a virtual PC/SC reader, i.e. by activating a PC/SC driver that is not tied to an actual USB hardware. This is the very same virtual PC/SC driver as the one used by PCSCBridge, SpringCard solution to support network and BLE PC/SC couplers. Therefore, starting and stopping SCardSniffer2 is likely to impact the operation of PCSCBridge. Please consider using SCardSniffer2 with USB couplers only.
2. SCardSniffer2 must have administrative privileges to install (and later remove) the virtual PC/SC reader. You’ll not be able to install nor use the application if you are not allowed to become an administrator to your computer.
Downloading and installing
SCardSniffer2 is available at https://www.springcard.com/en/download/find/file/sg21196.
Just download and execute the setup file to install SCardSniffer2.
Using SCardSniffer2
To explain how SCardSniffer2 works, we’ll be using PcscDiag2, a basic application available in the SpringCard PC/SC QuickStart.
The PC/SC QuickStart is available at https://www.springcard.com/en/download/find/file/sq13163.
Situation before launching SCardSniffer2
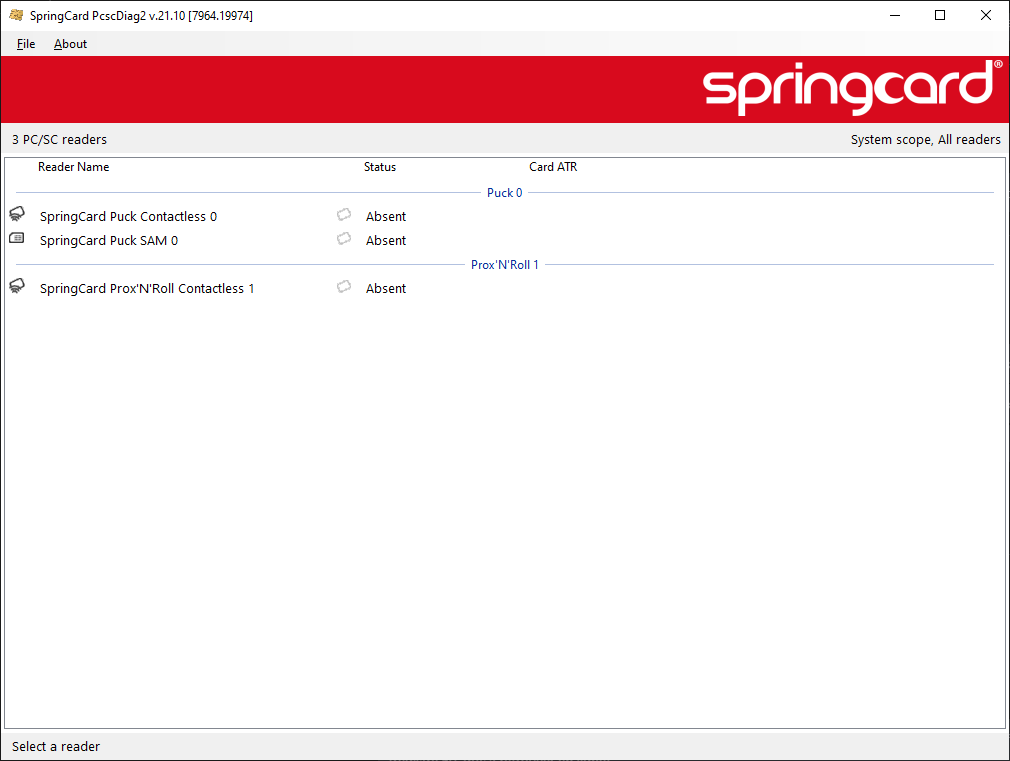
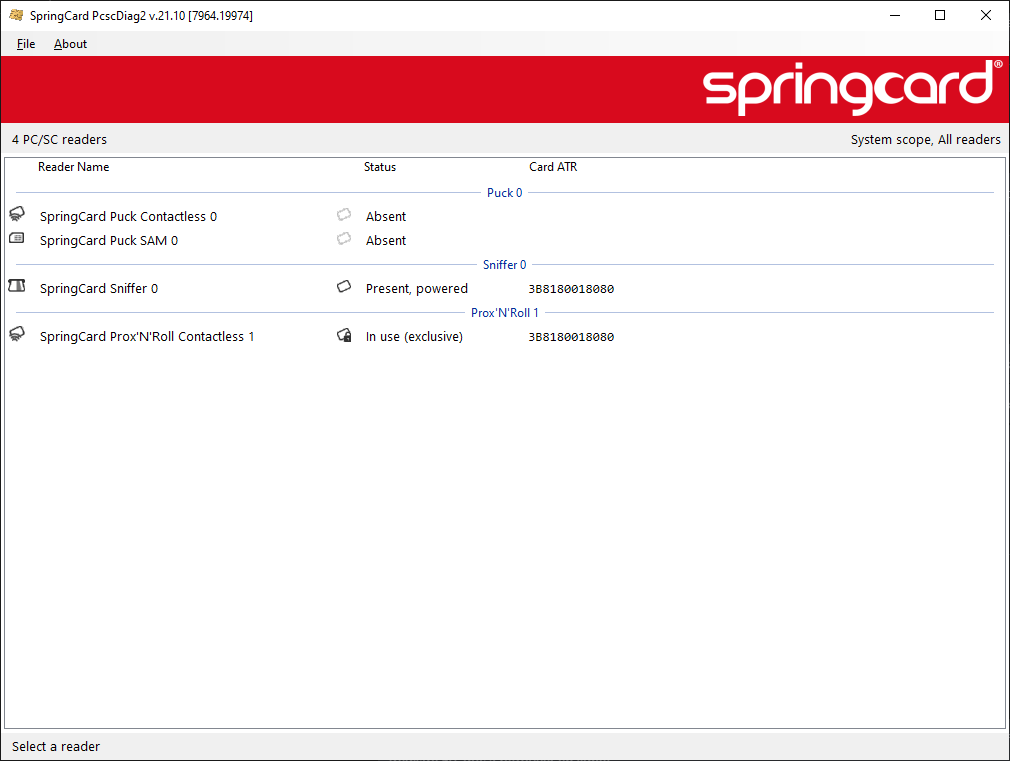
At first, PcscDiag2 shows that we have 2 PC/SC devices / 3 smart card readers connected:
Situation with SCardSniffer2 running
Now, let’s start SCardSniffer2.
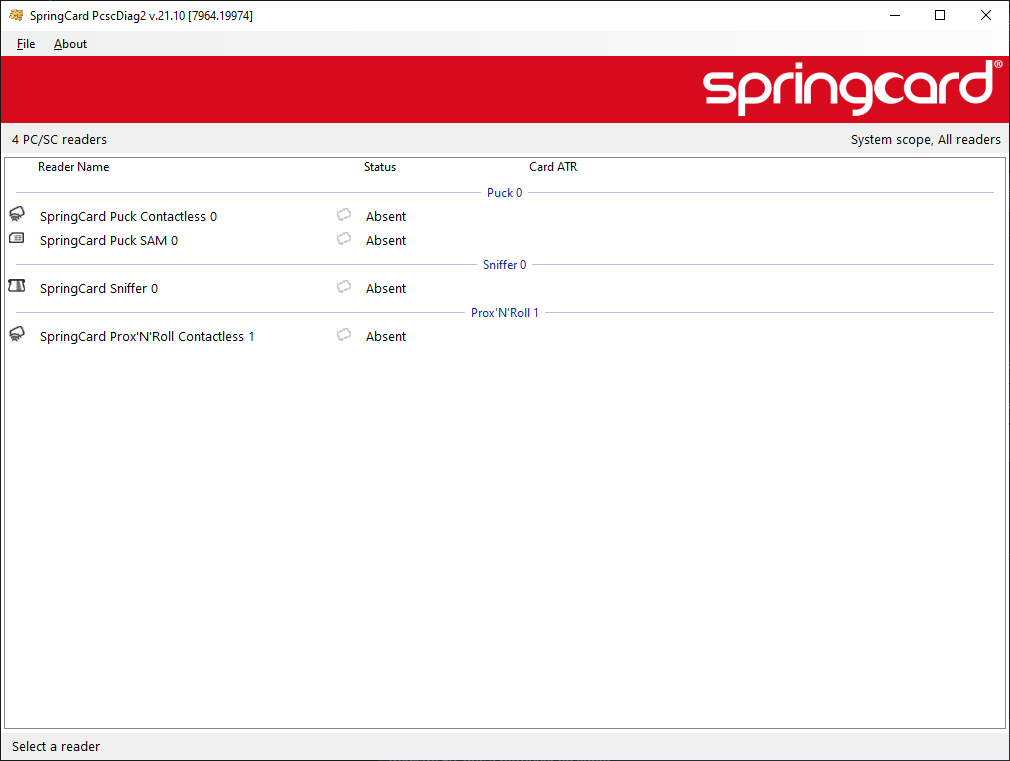
A new virtual PC/SC reader is installed after a few seconds. Its name is SpringCard Sniffer 0 (the number may be above 0 if you are running PcscBridge, since they share the same virtual driver).
Configuring and starting the spy
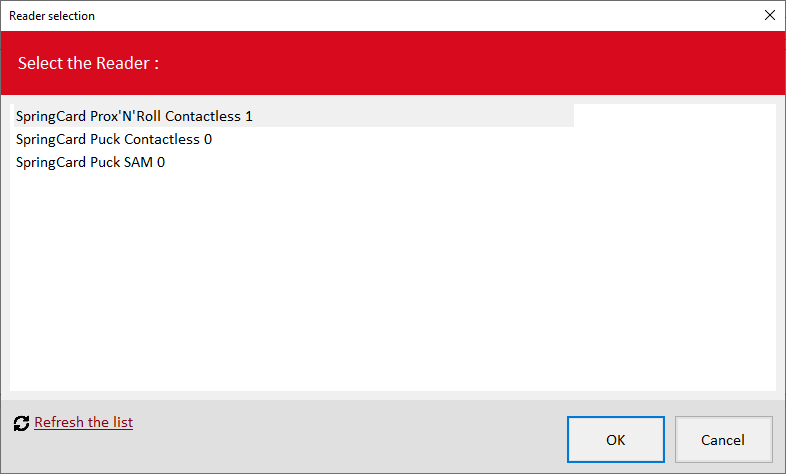
In SCardSniffer2, you must select the reader to spy: click Change over the Reader to spy edit box, or Select reader under the Actions menu.
NB: of course you can’t spy the virtual reader itself!
Once the reader has been selected, click the Play button to start recording the exchanges going through the virtual reader.
Smart card insertion
Insert a smart card on the reader you are spying.
In our example, we place an NXP Desfire contactless card over the Prox’N’Roll antenna.
Immediately,
1. PcscDiag2 shows that the card on the Prox’N’Roll has been reserved: the status is In use (exclusive). this is SCardSniffer2 that takes a an exclusive access to the “real card”.
2. PcscDiag2 also shows that a card with the same ATR has been inserted in the SpringCard Sniffer 0 virtual reader. This is SCardSniffer2 doing its job of relaying the status of the real reader to the virtual reader.
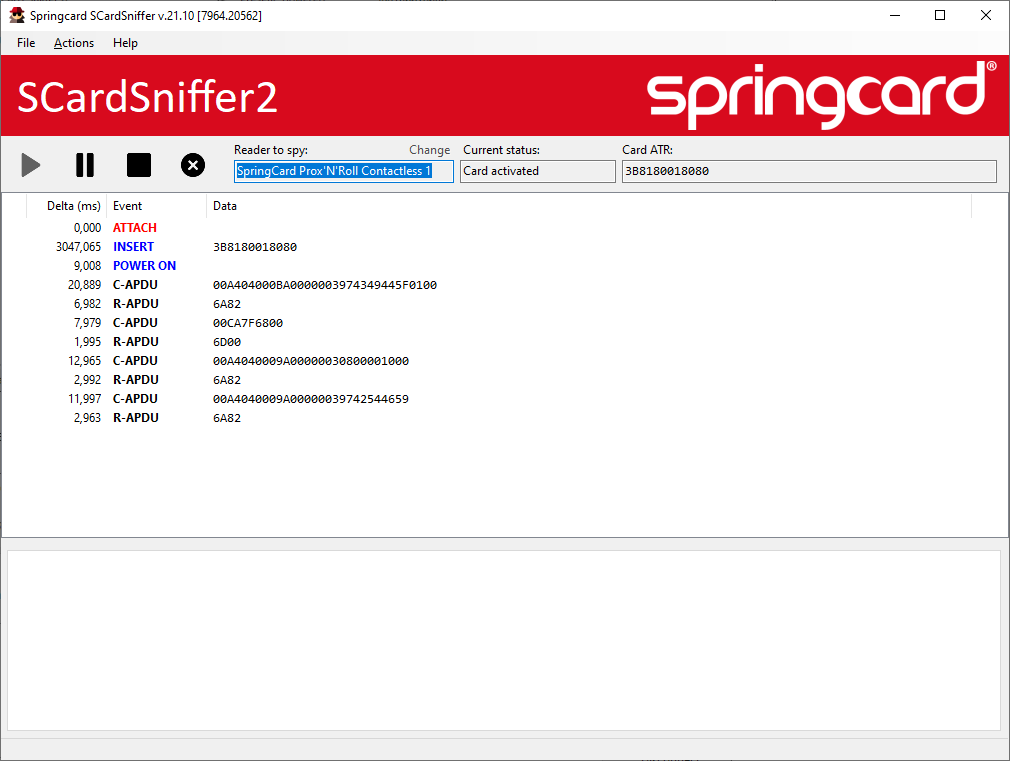
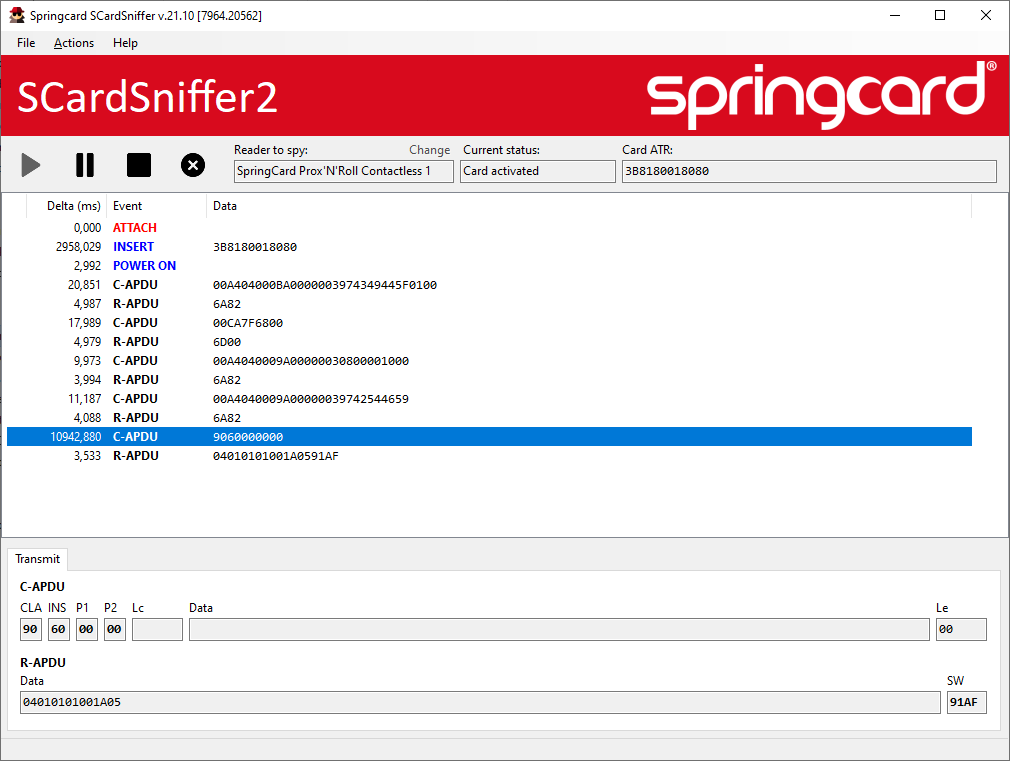
Let’s have a look at SCardSniffer2: it shows that a card has been inserted and powered on, and that some APDU have already been exchanged (command/response couples).
NB: this sequence of APDUs shows that the certificate propagation service is running on this computer. See the article about PCSCCheck for more details regarding the role of this service (and how to disable it).
Sending an APDU to the card
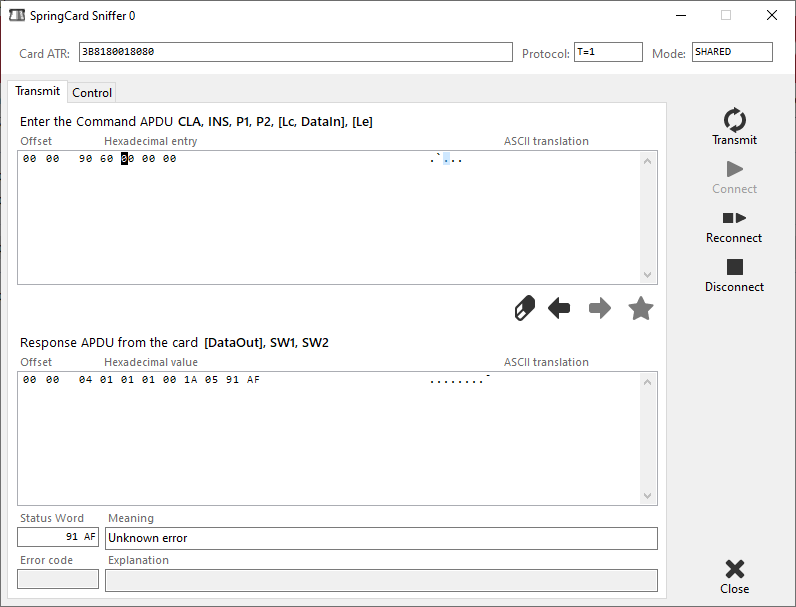
In PcscDiag2, we get a connection to the card in the virtual reader and send an APDU.
In our example, we send 90600000, the Desfire GET VERSION instruction wrapped in a valid ISO/IEC 7816-4 command.
The Desfire card replies with the first part of its VERSION string and 91AF as Status Word (SW).
Back to SCardSniffer2, we could retrieve this exchange at the end of the stream.
A more complex example
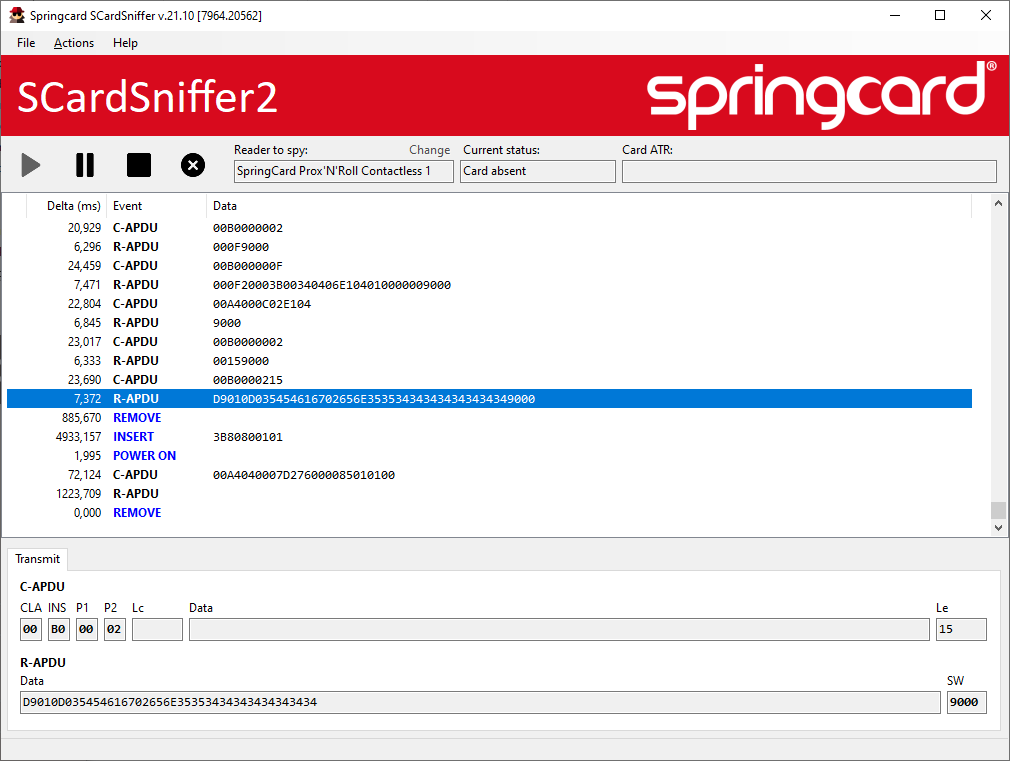
In the screenshot below, we use NfcTagTool, another application from the SpringCard PC/SC QuickStart, to read the Desfire card that is formatted as a NFC Forum Tag (Type 4).
This shows a longer sequence of APDUs. Click one APDU in the list (either the command or the response) to view the detail of the exchange.
Seen from the other application (NfcTagTool is this case), there’s no difference between working with the real reader and working with the virtual reader, apart than choosing the right one in the settings:
NB: to be completely honest, there’s a small difference: going through the SpringCard Sniffer virtual driver and the SCardSniffer2 application is likely to slow down the card transaction by a few milliseconds at every exchange, but in most situations this is absolutely unnoticeable.