The aim of this tutorial is to configure a SpringPark as a Network SmartReader/MQTT client with a mosquitto broker. The SpringPark in this configuration acts as an MQTT client (using TLS). It sends its tags to the mosquitto broker hosted at mqtt.springcard.com.
For this howto, we will assume that:
- your SpringPark is using a default (from factory) configuration.
- you have some networking basis.
- you have some MQTT basis.
To know how to configure the network or the basic MQTT client in the Springpark you can read theses articles:
- How to use a SpringCore network device as a smartreader MQTT client
- How to setup and use a SpringPark as a SmartReader over TCP
Configuring the SpringCore device for operation with mqtt.springcard.com
To load the configuration inside the Springpark, you will need the SpringCoreConfig utility.
It is possible to directly fetch and configure your device with the following command:
SpringCoreConfig --url https://docs.springcard.com/books/SpringCore/Appendixes/PKI_keys_and_certificates/TLS_client_with_MQTT/springcore-mqtt-springcard.json --network=192.168.1.22
The contents of the configuration file will look like below:
You may also download the springcore-mqtt-springcard.json file manually and edit its content as required.
Then use SpringCoreConfig to configure your device with the file you edited as seen below.
Once configured, the device will reboot.
Observing the events on the MQTT broker
The first thing to to after is to see if your device is connected to rthe broker is to go to the website mqtt.springcard.com which use a websocket to connect to the broker ans see all messages posted.
The websocket is only avalaible via localhost so you will need to connect to the real MQTTS port (8883) with a valid certificate if you want to access the topics. This matter, will be discussed later, for the moment we will see how everything is architectured.
Understanding the MQTT+TLS communication and authentication scheme
La magie derrière cette démo : grandes lignes du fonctionnement de TLS, utilisation d’un certificat client, architecture PKI SpringCard et certificats concernés
The aim of the TLS is to etablish a ciphered tunnel and a mutual authentication between a client and the broker.
TLS use X.509 certificates and support multiples cryptographic algorithms.
In our case, we need one Root CA (“SpringCore Root CA”) and multiples intermediates CA used to sign the differents certificates.
Here is the purpose of each intremediate CA:
- SpringCore Cloud CA: is used for the certificate that will be put on the broker.
- SpringCore Client CA: is used to generate the certificate of each device, each device can only read and write to a subset of topics associated to his client ID equal to the Common Name of his certificate
- SpringCore Watch CA: is used for the certificate “Watcher” that can subscribe to all the topics but cannot publish in any of them
- SpringCore Control CA: is used for the certificate “Control” that have fulle R/W access to all the topics
Below is the diagram of the SpringCore PKI architecture:
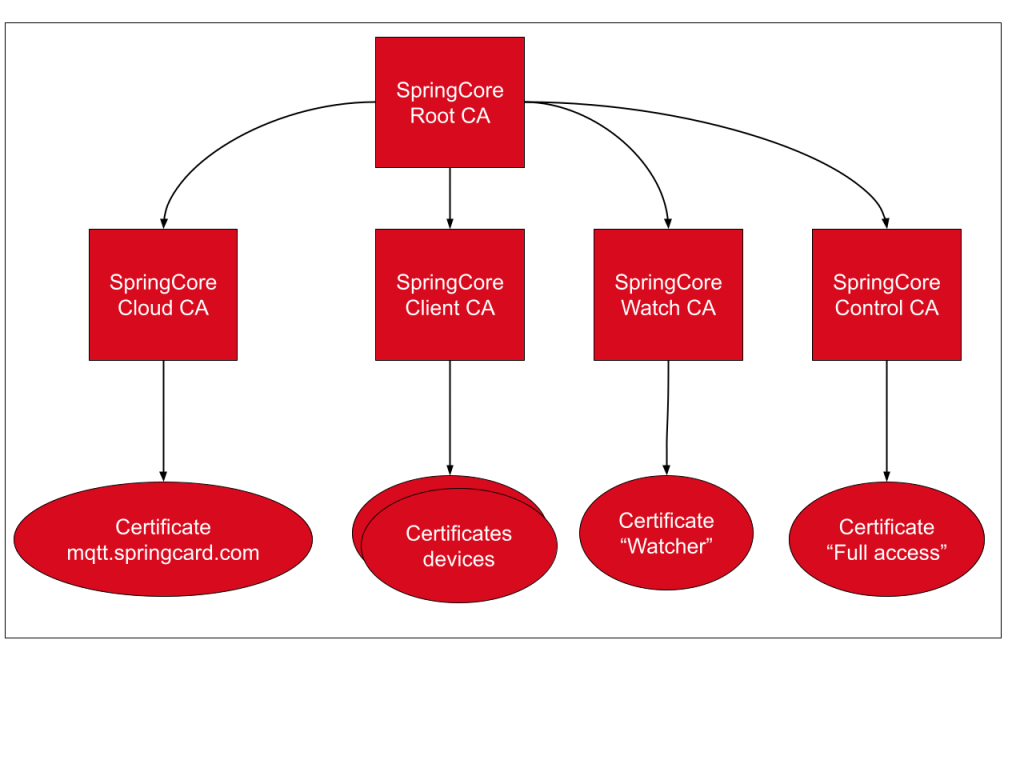
The ACLs evoqued before are not directly handled by the mosquitto broker but by a plugin developped by SpringCard.
Using others MQTT clients to connect to the MQTT+TLS broker
To connect to the broker with any client you will need some informations:
- the host (mqtt.springcard.com)
- the port (MQTTS standart port: 8883)
- the topic to subscribe to/publish
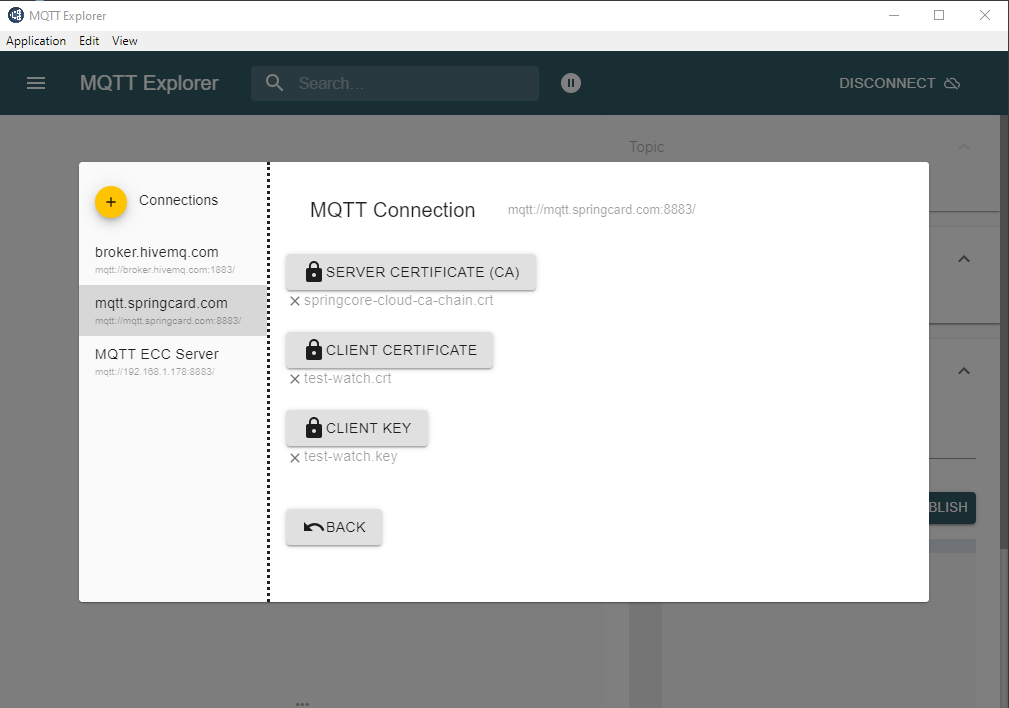
- The server’s certificate CA (chained with the Root CA)
- the client’s certificate
- the client’s certificate key
- a client ID matching the Common Name of the client’s certificate
The certificates are at the end of this article.
You can use any MQTT client supporting TLS like MQTT Explorer.
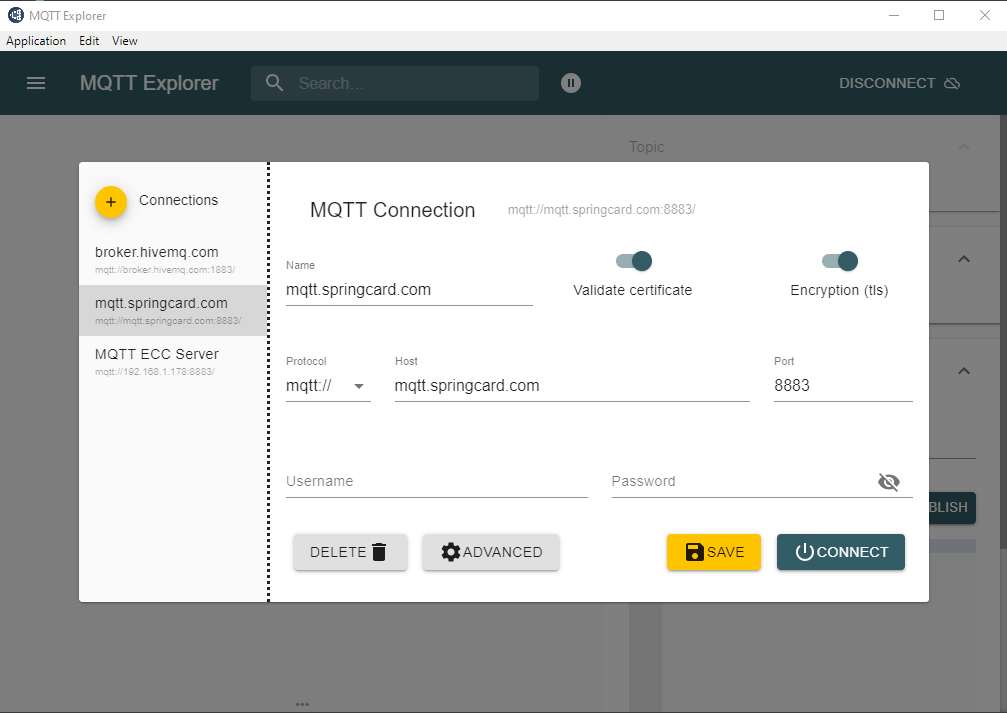
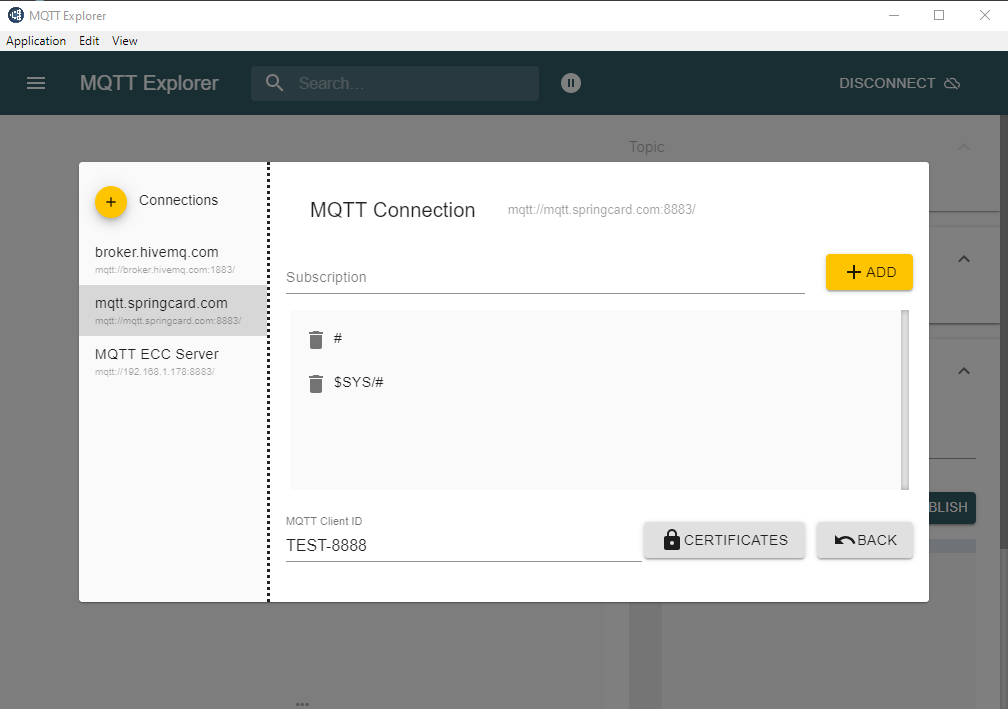
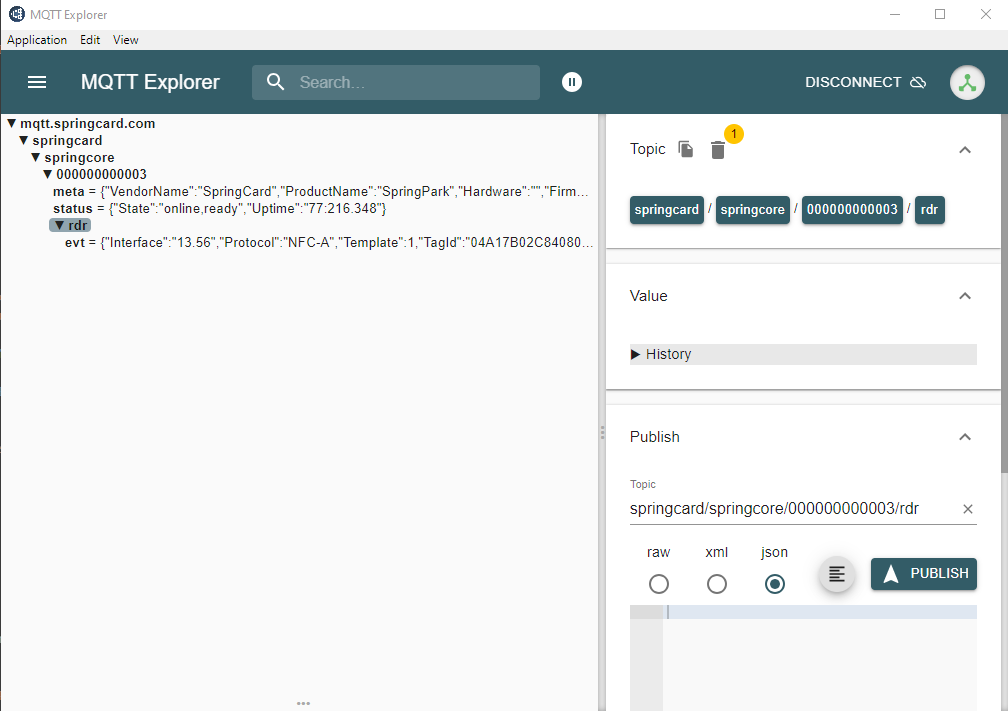
Another tool is mosquitto_sub/mosquitto_pub, which must be used with different parameters.

Implementing your own MQTT+TLS broker and accepting SpringCard’s certificates
If you want to set up your own MQTT broker with Mosquitto, you can have a look at this tutorial which is far more complete. It also help you to configure your SpringCore network device.
The tutorial is cut in 4 parts, from the basics to a more complex architecture
- Use a local broker without encryption
- Use a certificate on the broker’s side
- Use TLS on the server’s side and the client’s side (with its default key and certificate)
- Use TLS on the broker and the client’s side with your own certificates
Custom PKI architectures and advanced implementations
This conclude this article, but there are still many things to see.
For example we could see how to:
- Configure a broker and a client with your own certificates in Mosquitto
- Use MQTT websockets
- Implement your own Mosquitto plugin to handle the ACLs with the intermediates CAs
To know more about these topics you can contact us at info@springcard.com.
You can also read this tutorial for basics about SpringPark and broker configuration with your own certificates.